Security in
5G-Enabled Internet of Things Communication: Issues, Challenges, and
Future Research Roadmap - TACS
Evolution/generations of mobile communication system

Key Performance
Indicators for 5G

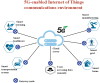
Network model
of 5G-enabled IoT environment
Classification
of security protocols in 5G-enabled IoT communications
environment.





5G mobile
communication systems promote the mobile network to not only
interconnect people, but also interconnect and control the
machine and other devices. 5G-enabled Internet of Things (IoT)
communication environment supports a wide-variety of
applications, such as remote surgery, self-driving car, virtual
reality, flying IoT drones, security and surveillance and many
more. These applications help and assist the routine works of
the community. In such communication environment, all the
devices and users communicate through the Internet. Therefore,
this communication agonizes from different types of security and
privacy issues. It is also vulnerable to different types of
possible attacks (for example, replay, impersonation, password
reckoning, physical device stealing, session key computation,
privileged-insider, malware, man-in-the-middle, malicious
routing, and so on). It is then very crucial to protect the
infrastructure of 5G-enabled IoT communication environment
against these attacks. This necessitates the researchers working
in this domain to propose various types of security protocols
under different types of categories, like key management, user
authentication/device authentication, access control/user access
control and intrusion detection. In this survey paper, the
details of various system models (i.e., network model and threat
model) required for 5G-enabled IoT communication environment are
provided. The details of security requirements and attacks
possible in this communication environment are further added.
The different types of security protocols are also provided. The
analysis and comparison of the existing security protocols in
5G-enabled IoT communication environment are conducted. Some of
the future research challenges and directions in the security of
5G-enabled IoT environment are displayed. The motivation of this
work is to bring the details of different types of security
protocols in 5G-enabled IoT under one roof so that the future
researchers will be benefited with the conducted work.
5G is
the fifth generation mobile communication systems which promotes
the mobile network to not only interconnect people, but also
interconnect and control the machine and other devices (i.e.,
smart devices). It improves the performance and efficiency which
capacitate the user experiences. 5G delivers peak rates up to 10
Gbps, “ultra-low latency” and “massive capacity” which provides
the consistence and uniform service to the user. It is a
wireless networking architecture which was built on the
“802.11ac IEEE wireless networking standard” and aims to improve
the data communication speeds by up to three times as compared
to its antecedent “4G- IEEE 802.11n”. Read the full research at:
|
About TACS
TACS
Consulting Delivers The Insight and Vision on Information
Communication and Energy Technologies for Strategic Decisions.
TACS is Pioneer and Innovator of many Communication Signal
Processors, Optical Modems, Optimum or Robust Multi-User or
Single-User MIMO Packet Radio Modems, 1G Modems, 2G Modems, 3G
Modems, 4G Modems, 5G Modems, 6G Modems, Satellite Modems, PSTN
Modems, Cable Modems, PLC Modems, IoT Modems and more..
TACS consultants conducted fundamental scientific research in
the field of communications and are the pioneer and first
inventors of PLC MODEMS, Optimum or Robust Multi-User or
Single-User MIMO fixed or mobile packet radio structures in the
world.
TACS is a leading top consultancy in the field of Information,
Communication and Energy Technologies (ICET). The heart of our
Consulting spectrum comprises strategic, organizational, and
technology-intensive tasks that arise from the use of new
information and telecommunications technologies. TACS Consulting
offers Strategic Planning, Information, Communications and
Energy Technology Standards and Architecture Assessment, Systems
Engineering, Planning, and Resource Optimization.
|
TACS is a leading top consultancy in the field of information, communication
and energy technologies (ICET).
The heart of our consulting spectrum comprises strategic,
organizational, and technology-intensive tasks that arise from the use of new
information, communication and energy technologies.
The major emphasis in our work is found in innovative consulting and
implementation solutions which result from the use of modern information,
communication and energy technologies.
TACS
- Delivers the insight and vision
on technology for strategic decisions
- Drives
innovations forward as part of our service offerings to customers
worldwide
- Conceives
integral solutions on the basis of our integrated business and technological
competence in the ICET sector
- Assesses technologies and standards and develops
architectures for fixed or mobile, wired or wireless communications systems
and networks
- Provides
the energy and experience of world-wide leading innovators and experts in their fields for local,
national or large-scale international projects.
|